Blackshades Net Can Best Be Described as a Wrapper
E a bond order of 2. The movement of molecules with their concentration gradient from areas of higher concentration to areas of lower concentration.
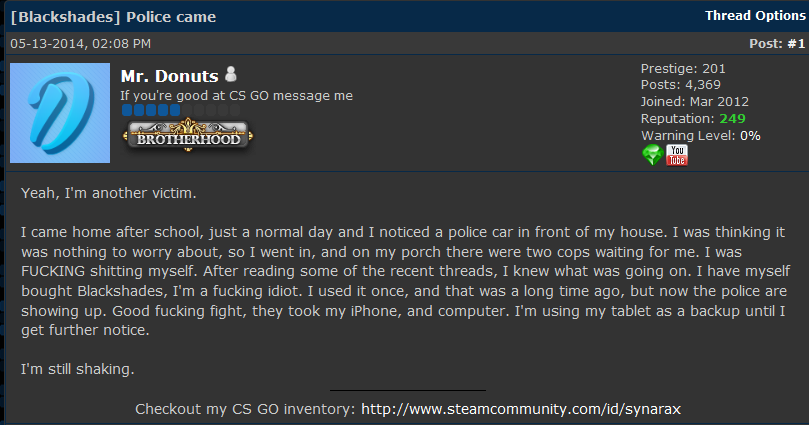
Blackshades Trojan Users Had It Coming Krebs On Security
RAT Bot Wrapper DDoS Tool The two types of honeypots include.
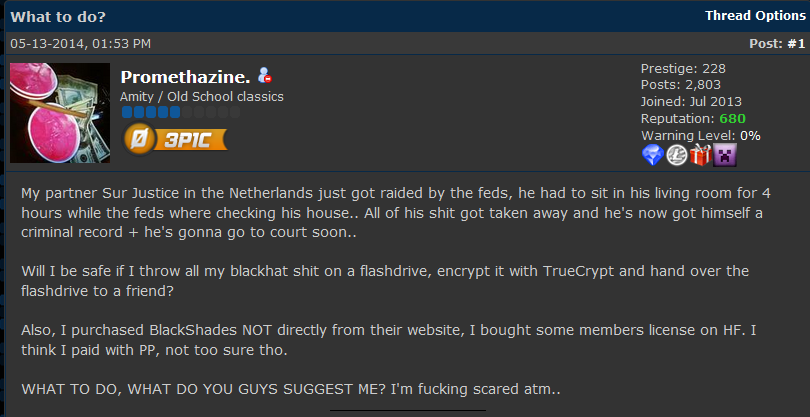
. Young-of-year shad are now about 2-3 inches long and programmed to swim en masse upstream. Is the application visible. Question 78 0 1 point BlackShades Net can best be described as a.
When assessing threats to a system what three factors should you consider. In reference to crowdfunding a backer is best described as. C a trigonal planar geometry about the C atom.
A octahedral geometry about the carbon. Predators both piscatorial and of the feathered variety are aware of this migration with the entire scheme of things coming together in what can only be described as a feeding frenzy. Starting at 100 60 British pounds according to the BBC.
What name does the application have. Simple and flat design websites serve as a rulers in the web design scenario. How much traffic the system gets the security budget and the skill level of the security team.
Question 73 1 point. OwnFone users can now create a phone with Braille buttons. Choose all that apply Question 73.
DDoS Tool RAT Question 80 0 1 point Buffer overflow attacks allow an attacker to modify the _____ in order to control the process execution. The carbonate ion CO 32- can best be described as having. TrueFalse Third-party cookies can be stolen and used to impersonate the user while first-party cookies can be used to track the browsing or buying habits of a user.
Logic holds that black plastic should absorb more heat and speed fermentation he adds. Choose all that apply Question 73 options. Bot Wrapper DDoS Tool RAT.
On a local host. B a tetrahedral geometry about the C atom. JavaScript HTML VBScript Flash Question 74 1 point.
An African Headwrap or African Head Wrap two words is a piece of cloth tied around the head in an intricate style. BlackShades Net can best be described as a. IPS IDS low interaction.
Lines are used in art to indicate. Question 73 1 point With Cross Site Scripting attackers can inject malicious ____. Question 72 1 point BlackShades Net can best be described as a.
Explicit session ID Cloned session Hash BlackShades Net can best be described as a. Maltrail is a malicious traffic detection system utilizing publicly available blacklists containing malicious andor generally suspicious trails along with static trails compiled from various AV reports and custom user defined lists where trail can be anything from domain name eg. On a local area network.
Access control One job that a router performs is that of gatekeeper which means that it can be configured to only allow certain packets access into the network based on a. - motion - texture - color - line - shape. Depending on plastic wrap quality and wrapping techniques you can expect 15 to 25 of bales to have some degree of spoilage says Jamie Patton University of Wisconsin County Extension agent.
- motion - time - mass - line - light. UK-based OwnFone a company that lets users design their own mobile devices introduced what its calling the worlds first Braille phone. Available in many colors and patterns fabrics and sizes headwraps are usually about 60-72.
Baleage allows harvesting high-moisture hay with minimal harvest loss. Wireshark can be used in a variety of ways however the most common configuration for Wireshark and the configuration that you ran in the lab has the software running. The name and icon for the installer application can be freely chosen by you.
In the simplest terms Wireshark is used to capture all. Blackshades has the ability to infect and hack multiple computers from the release of a bait that the hacker can make use of an improved version of blackshades was released shortly after the original release of the primary version when hacking organizations like Octagonun and Cyber-Sec decided to develop special features for coupling to the. It can be a strong cultural statement a fashionable accessory or a smart fix for those days when you dont want to style your hair.
We do our best to keep the detection rate as low as possible but we can not prevent false positives. The client application has the name BlackShades. Which of the visual elements can best be described as the path of a moving point.
Bot Wrapper DDoS Tool RAT Question 73 1 point With Cross Site Scripting attackers can inject malicious ____. Crowdfunding can best be described as. Capital from a large audience usually through the internet.
Clean Black and white websites are trending of this year. Spring is not a good time to be a young shad on the Mississippi River. Net worth over 1 million or income over 200K.
From a probe or hub. So im going to show you cool examples of web design inspiration and Today its all about these 16 best clean black and white website designs. 16 Best Clean Black White Website Design Examples.
Biology questions and answers. Part 15 Active transport can best be described as Multiple Choice the diffusion of water from areas where water concentration is higher to areas where water concentration is lower. D a total of 22 valence electrons.
Mashable - 20 May 2014 0232. 1134 Lab Visualizing the Black Hats Instructor Version CCNA Cybersecurity Operations Cyber Ops v11 Exam Answers 2020-2021 download pdf file. During the 20th century which of the following became a recognized element of art.
Which layer is responsible for determining the best path a packet should travel across an internetwork. In a peer-to-peer configuration. BlackShades Net can best be described as a.
Learn this topic by watching Molecular Geometry Concept Videos. The systems attractiveness the information contained on the system and how much traffic the system gets. What is a typical investment range for.

Blackshades Trojan Users Had It Coming Krebs On Security
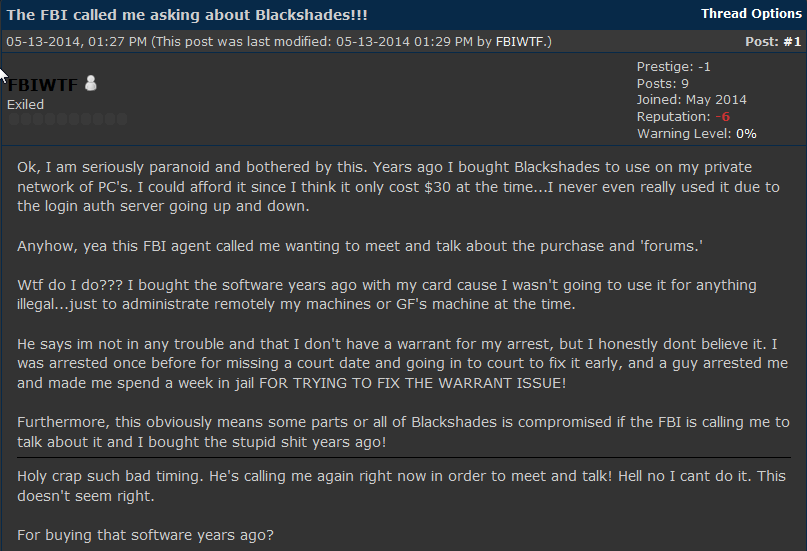

No comments for "Blackshades Net Can Best Be Described as a Wrapper"
Post a Comment